 Mobile Computing and Sensing
Mobile Computing and Sensing
Vehicular Technology.
As more vehicles take part in the transportation system in recent years, the development of vehicular technology becomes a corner stone to improve driving safety.
In this project, we exploit two main areas, i.e., sensing vehicle dynamics and monitoring driving behaviors. For sensing vehicle dynamics, we exploit the motion
sensors on mobile devices to sense the speed, lane condition and abnormal driving condition of vehicles. For monitoring driving behaviors,
we explore acoustic signals to capture the abnormal behavior of drivers and track steering wheel angle of drivers in real time, and explore mmWave signals to realize heartbeat electrocardiograph revocery for monitoring driver's health condition. Related works are published in ACM SenSys’13,
IEEE InfoCom’14,16,17,22, IEEE SECON’15,18, IEEE TMC.
Human-Machine Interactions.
Human-computer interaction (HCI) is a multidisciplinary field of study focusing on the design of computer technology and,
in particular, the interaction between humans (users) and computers/mobile devices/appliances. HIC significantly dominates the satisfactory of user
experience while using specific systems. In this project, we explore the scrolling human-computer interactions during browsing
to infer user interest about the browsing content through modeling the relationship between scrolling and user interest with naïve
Bayesian and convolutional neural network techniques. Also, we investigate the relationship between user experience and color
scheme during browsing and adapt it through sensing the ambient light. Relative studies are published in ACM UbiComp'19,
ACM SenSys'15, IEEE TMC, etc.
 Smart Healthcare
Smart Healthcare
Vital Signals.
Fine-grained breathing and heartbeat patterns are critical indicators of the wellbeing of people. However, existing studies on vital signal monitoring either require active user participation
of wearing special sensors, or need relatively quiet environments. In this project, we leverage acoustic signal generated by mobile devices to estimate the fine-grained breathing waveform of users,
which can separate breathing from other body movements and can be done in noisy environment like driving vehicles. Also, we exploit millimeter wave to detect the tiny body movement
caused by heartbeats of users and further recover the fine-grained ECG of users. Related work is published in ACM MobiSys'19 and IEEE INFOCOM'22.
Some Past Projects
Cloud Security. Data sharing in the cloud, fuelled by favourable cloud technology trends, has emerging as a promising pattern in regard to enabling data more accessible to users in a convenient manner. To achieve data sharing, enterprises and customers in increasing numbers keep their data stored into cloud server. In this project, we focus on seeking a solution that allows secure and effective access to the cloud data and data privacy of searchable symmetric encryption (SSE) in cloud computing.
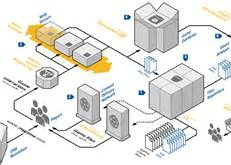
Cloud Resource Schedule. Benefiting from the pay-per-use pricing model of cloud computing, many companies migrate their services and applications from typical expensive infrastructures to the cloud. However, due to fluctuations in the workload of services and applications, making a cost-efficient VM configuration decision in the cloud remains a critical challenge. In this project, we first design a double auction mechanism to balance the profits of both cloud provider and users. Then, we model an optimization problem aiming to minimize the VM configuration cost under the constraint of migration delay. Taking advantages of Lyapunov optimization techniques, we propose a mix scale online algorithm which achieves more cost-efficiency than that of scale out strategy.

 Internet of Things (IoT)
Internet of Things (IoT)
 Cyber Security and Privacy
Cyber Security and Privacy

 Mobile Computing and Sensing
Mobile Computing and Sensing

 Smart Healthcare
Smart Healthcare

